In a world where internet cowboys and threat actors are out to breach your network defenses and steal all your precious personal and organisational data, who can you trust? Furthermore, how do you ensure trusted users remain trustworthy?
Zero Trust is a network security model and mindset that upholds a view that no one (users or devices), whether inside or outside a network, should be trusted by default.
To help achieve this, Zero Trust comprises three main principles:
- Never trust, always verify when it comes to authentication and authorization.
- Implement the Principle of Least Privilege (PoLP).
- Assume your network is breached.
The Principle of Never Trust, Always Verify
In traditional network access methods, once a user is authenticated (their identity is confirmed, typically by username and password) no further attention is given to what resources are accessed, the context in which the resource is accessed, or what type of device used to access those resources.
This introduces a level of risk as if the identity is compromised or hijacked, attackers can leverage this to access substantial portions of the data and systems on your network, potentially indefinitely as an Advanced Persistent Threat (APT).

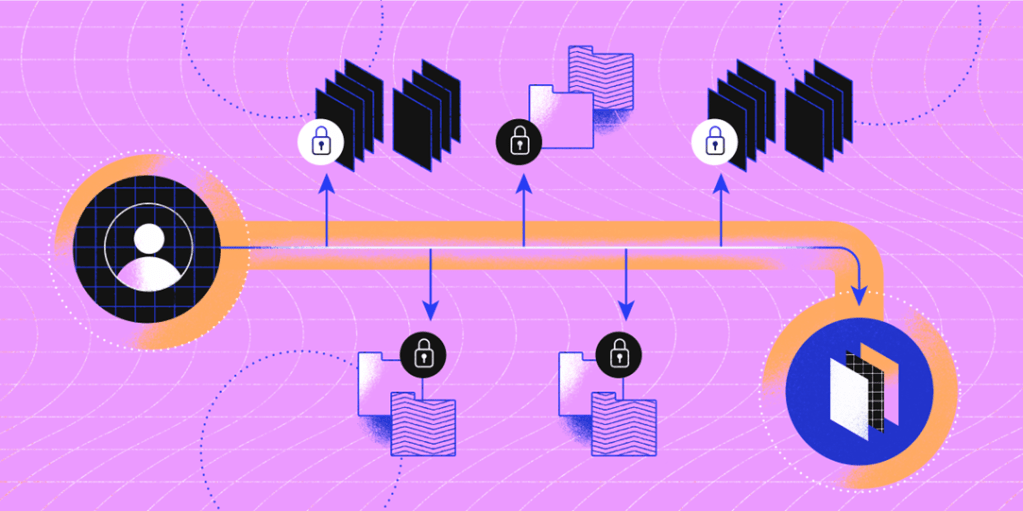
The Zero Trust model bolsters the security and effectiveness of authentication and authorization methods by deriving trust from a combination of identity and context-based cues:
For secure id authentication, Multifactor Authentication (MFA) is deployed – this requires using a username and password (i.e. something you know) and a variety of other methods such as a palm vein scan or one-time use passcode (i.e. something you have), making it difficult for an attacker to obtain all the information needed to pose as a valid user.
Context-based cues are also used in determining authentication and authorization level. These can include:
- Geolocation – Restricting access based on location.
- Time & Date – Restricting access during non-business hours.
- Security Posture of Device – Restricting access to endpoints (devices) that do not meet security requirements, this could be based on the device’s operating system version, installed software, assessed risk level, etc.
Together, MFA and context-based cues provide enhanced security over who can gain access to the network and its resources.
The Principle of Least Privilege
If you invited a guest over for dinner, would you give them the keys to your home? Unless you are a particularly open and trusting individual, you would greet them at the door, confirming their identity. For the duration of their visit, you would then monitor them and control their access, allowing them, say, use of the bathroom where they can use the toilet and wash their hands, but not use your toothbrush or repaint your walls a different colour; or the kitchen where they could use the plates and cutlery you provide, not pocket the silverware for themselves. This is the Principle of Least Privilege (PoLP) in action.
Privileged Access Management (PAM) is an Information Security (InfoSec) safeguard where a user or device identity & role determines the level of authorization the user or device has over network resources. Through PAM, you can limit what data, services, and devices a client can access and what permissions they have regarding those resources, such as copy, configure, transfer, and read/write.
For example, Beatrice from Public Relations requires access to the company’s social media management platform, but she should not have access to view and modify the company’s database of financial records. In this scenario, PAM can be used to define which specific network resources, be they apps, services, or data, Beatrice can access; her unique user identity could be assigned to a preconfigured ‘Public Relations’ role or group, outlining rules for what access and privileges she has.
A critical component of the PoLP is to define the protect surface by identifying network resources, assessing the confidentiality of data-at-rest and data-in-transit, and determining which roles need what level of access.
The Principle of Assume Your Network is Breached

The assume breach principle has you embrace paranoia and envisage every worst-case scenario that could potentially befall your security measures to anticipate and prepare with the appropriate contingency plans.

Beatrice is now branded as an insider threat capable of intentionally or unintentionally compromising network resources and security measures.
This principle emphasizes dealing with risks pre-emptively by:
- Setting up and regularly testing appropriate measures for Disaster Recovery.
- Preventing sensitive data breaches and exfiltration with Data Loss Prevention (DLP) software.
- Incorporating Least Privilege and network Microsegmentation to impede privilege escalation and the lateral movement of attackers.
With the increasing reliance on data, networks, and devices for mission-critical business applications, implementing a network architecture built around strict authentication, access control, and risk mitigation/contingency is crucial in addressing modern security and compliance requirements.
In the next Cybersecurity Chunk, I’ll take a look at Zero Trust Network Access (ZTNA) to see how the Zero Trust principles are culminated into a deployable framework for secure remote network access.
~ G.G. May 2024




Leave a comment