Network Segmentation is the process of dividing a network into smaller, isolated networks based on purpose, users, or security requirements and provides a variety of benefits to network management, security, and optimization.
Implementing secure network segmentation requires careful setup and coordination across multiple networking layers, including:
· Data-link: Setup of VLANs through switches.
· Network: Subnets, firewall policies, ACLs.
· Application: SD-WAN, underlay & overlay networks, VPN tunnels.
Common in cloud and virtualization infrastructures, segments can be further divided into microsegments to help prevent VM escape/hopping and reduce the attack surface.
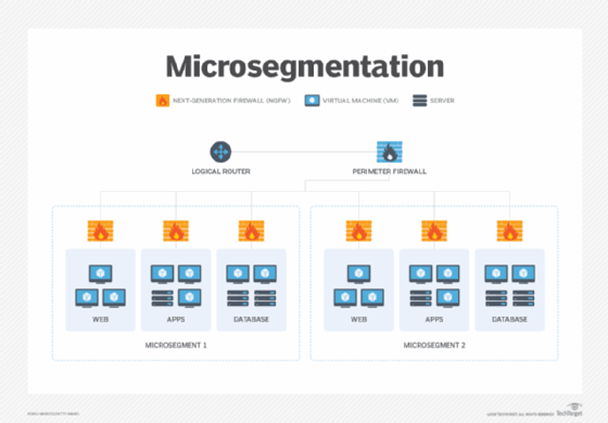
Benefits of Segmented Networks
Provide A Greater Ease of Network Management and Configuration: Having well planned and audited network segments allows us to easily focus management efforts on those segments. This improves administration and network visibility as segments are designed by function, business department, security requirements, etc.
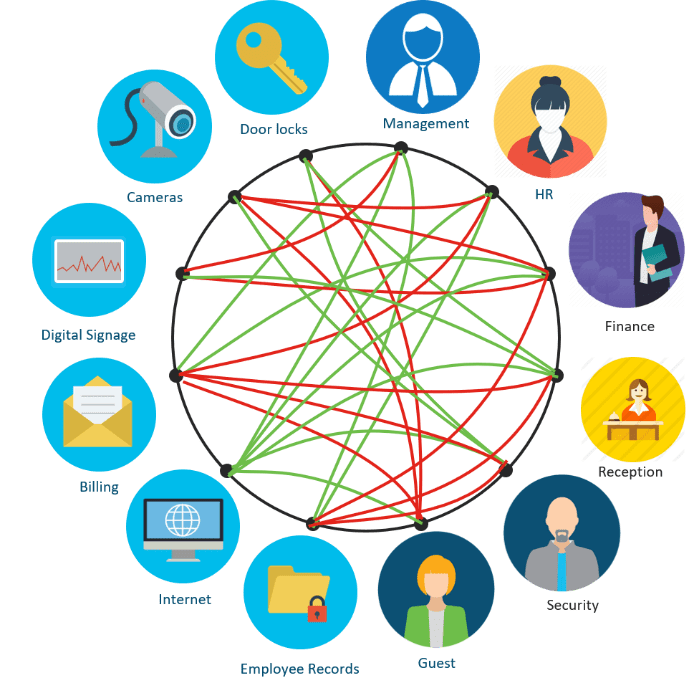
Network Optimization: Properly configured network segmentation can reduce the number of broadcast domains and can help manage and minimize network congestion.
Limit Attacks to a Specific Segment: If a breach occurs, network segmentation helps to impede the lateral movement of attackers by limiting them to a specific segment.

Greater Protection of Vulnerable Devices: Devices with little to no security mechanisms gain an abstract layer of protection from isolated network segments. It is common to place devices that do not meet security posture requirements, like IoT or guest devices, onto an isolated network segment indefinitely, or until compliance requirements can be met.
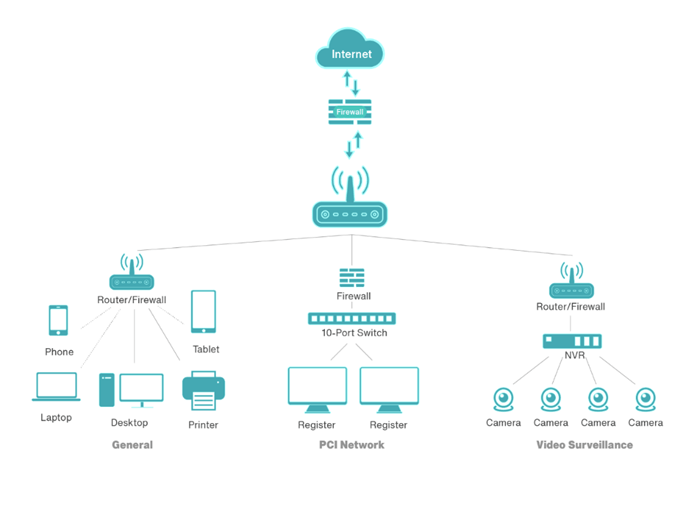
Accessing Segmented Networks
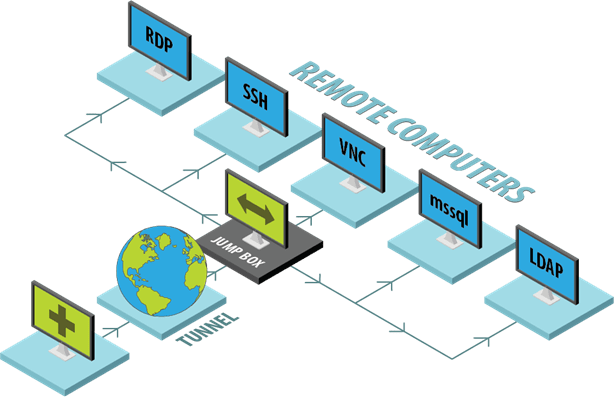
Jump Box/Jump Server/Jump Host: A device (usually configured with SSH) with enhanced access control and limited authorization which acts as a proxy to devices spanning multiple segments or security zones. Jump Boxes can also provide additional monitoring and logging tools. Careful consideration is needed when setting up secure jump boxes as misconfiguration presents an elevated risk of compromise.

Bastion Host: A hardened device which provides secure access to a segmented network from an external network e.g. a DMZ or outside of the internal firewall. A bastion host typically runs a single application or process (usually SSH) used to access the segmented network, reducing its attack surface.
A variety of VPN solutions also exist to access segmented networks.
~ G.G. May 2024




Leave a comment